Office365 Executive Inboxes Targeted In Multi-Million Dollar Hacking Scheme
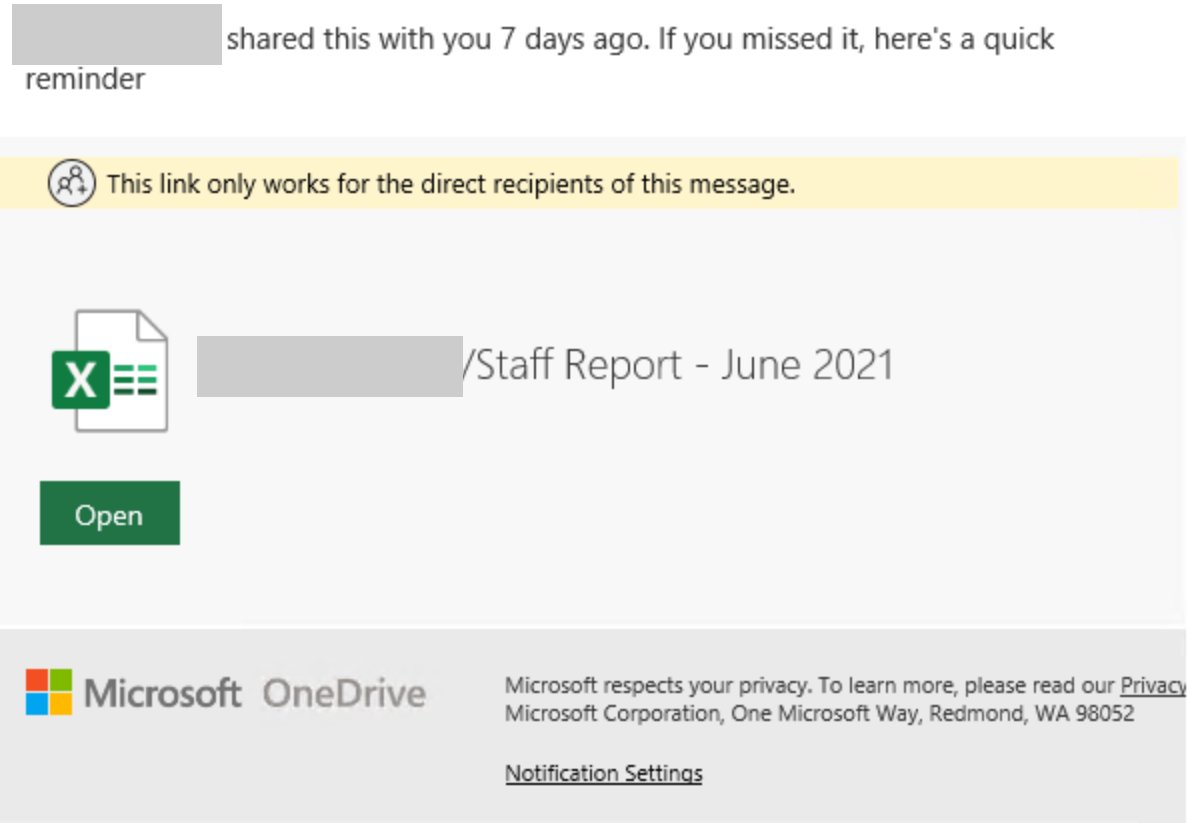
Table of Contents
Methods Used in Office365 Executive Inbox Attacks
Cybercriminals employ increasingly sophisticated techniques to compromise Office365 executive inboxes. These attacks often leverage a combination of methods, making them difficult to detect and prevent. The financial impact of these Office365 hacking schemes is staggering, underscoring the importance of proactive security measures.
-
Sophisticated Phishing Campaigns: Spear phishing attacks are a cornerstone of these schemes. Hackers craft highly targeted emails mimicking legitimate communications from known contacts, clients, or even internal colleagues. These emails often contain urgent requests, leveraging current events or confidential company information obtained through previous data breaches to increase their believability. The goal? To trick executives into revealing their credentials or clicking on malicious links.
-
Exploiting Weak Passwords: Credential stuffing, a technique where hackers use stolen credentials from other data breaches, is a common attack vector. If an executive uses weak or reused passwords across multiple accounts, their Office365 login is easily compromised. This highlights the critical need for strong password policies and password management tools.
-
Malware Deployment: Malicious attachments or links embedded in seemingly innocuous emails deliver malware directly onto the executive's computer. This malware often includes keyloggers, recording every keystroke, and remote access Trojans (RATs), giving hackers complete control over the infected system and potentially the entire company network. This can lead to extensive data theft and ransomware attacks.
-
Social Engineering Tactics: Highly skilled hackers often utilize social engineering techniques, manipulating executives through psychological manipulation. They exploit trust and urgency, creating scenarios where the executive feels compelled to act quickly without proper verification, leading to account takeover and further compromise.
Devastating Consequences of Office365 Executive Inbox Compromises
The consequences of a successful Office365 executive inbox compromise can be catastrophic, impacting far beyond the initial data breach. The financial losses and reputational damage can be crippling for organizations of all sizes.
-
Significant Financial Losses: These attacks frequently result in fraudulent wire transfers, invoice scams, and other financial crimes, leading to multi-million dollar losses. Hackers often exploit the authority of the executive to authorize these fraudulent transactions.
-
Data Breaches and Intellectual Property Theft: Access to executive inboxes exposes sensitive company data, including financial records, strategic plans, customer data, and valuable intellectual property. This data theft can cripple a company’s competitive advantage and lead to further legal and financial repercussions.
-
Reputational Damage: Public disclosure of a security breach severely damages a company's reputation, impacting investor confidence, customer loyalty, and future business opportunities. The loss of trust can take years to rebuild.
-
Legal Ramifications: Companies face significant legal repercussions, including hefty fines and lawsuits from regulatory bodies and affected parties for failing to meet data protection regulations and adequately protect sensitive data.
-
Business Disruption: Attacks disrupt operations, causing delays in projects, loss of productivity, and potential business interruption. The time and resources spent investigating and recovering from the breach can be incredibly costly.
Protecting Your Office365 Executive Inboxes
Protecting your Office365 executive inboxes requires a multi-layered approach combining technology, training, and policy. Implementing these measures is crucial for mitigating the risk of costly executive email compromise.
-
Implement Multi-Factor Authentication (MFA): MFA adds an essential layer of security, requiring a second form of verification beyond just a password. Even if a password is compromised, MFA prevents unauthorized access.
-
Invest in Robust Email Security Solutions: Advanced email security solutions are essential. Utilize solutions that employ anti-phishing, anti-malware, and sandboxing technologies to proactively detect and block malicious emails before they reach inboxes.
-
Conduct Regular Security Awareness Training: Regular, engaging security awareness training is critical, especially for executives. Educate employees on identifying phishing attempts, recognizing social engineering tactics, and practicing safe email habits.
-
Enforce Strong Password Policies: Implement and rigorously enforce strong password policies requiring complex passwords, regular changes, and the prohibition of password reuse. Consider leveraging a password manager to simplify this process for employees.
-
Implement Data Loss Prevention (DLP) Measures: DLP tools monitor and prevent sensitive data from leaving the organization's network, limiting the impact of a successful breach.
-
Develop an Incident Response Plan: A well-defined incident response plan is crucial. It outlines steps to quickly contain and mitigate the damage in case of a security breach, minimizing downtime and financial losses.
Conclusion
The targeting of Office365 executive inboxes in multi-million dollar hacking schemes underscores the critical need for proactive and robust security measures. By implementing multi-factor authentication, investing in advanced email security solutions, and conducting regular security awareness training, organizations can significantly reduce their risk of experiencing a devastating Office365 security breach. Don't wait until it's too late – protect your Office365 executive inboxes and your bottom line by taking immediate action to strengthen your cybersecurity posture. Learn more about securing your Office365 environment and preventing costly executive email compromise today.

Featured Posts
-
 Ted Lassos Revival Brett Goldsteins Resurrected Cat Analogy
Apr 24, 2025
Ted Lassos Revival Brett Goldsteins Resurrected Cat Analogy
Apr 24, 2025 -
 John Travolta Shares Moving Photo On Late Son Jetts Birthday
Apr 24, 2025
John Travolta Shares Moving Photo On Late Son Jetts Birthday
Apr 24, 2025 -
 High California Gas Prices Prompt Governor Newsoms Call To Action
Apr 24, 2025
High California Gas Prices Prompt Governor Newsoms Call To Action
Apr 24, 2025 -
 Od Djevojcice Do Zene Nevjerojatan Rast Elle Travolte
Apr 24, 2025
Od Djevojcice Do Zene Nevjerojatan Rast Elle Travolte
Apr 24, 2025 -
 Exclusive Probe Launched Into World Economic Forum Founder Klaus Schwab
Apr 24, 2025
Exclusive Probe Launched Into World Economic Forum Founder Klaus Schwab
Apr 24, 2025
