T-Mobile Data Breaches: $16 Million Fine Highlights Security Gaps
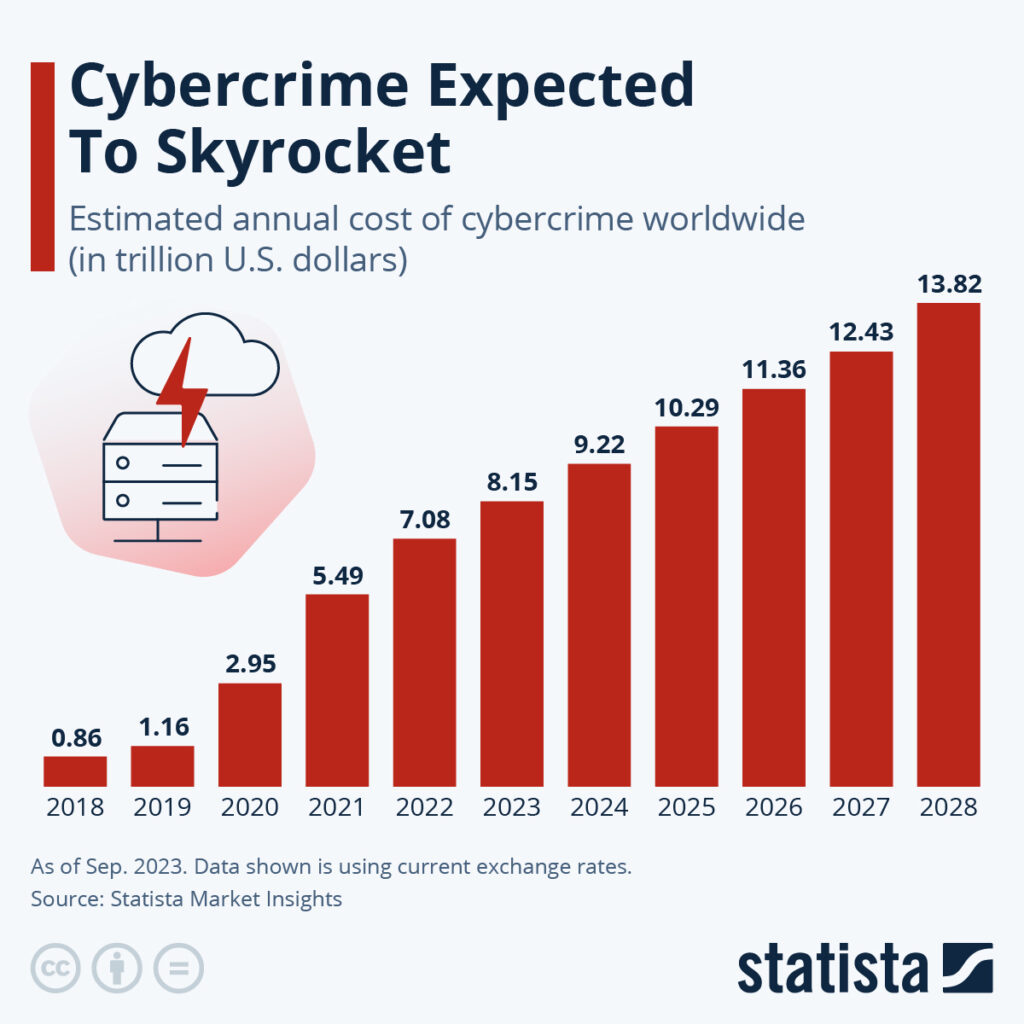
Table of Contents
The Extent of the T-Mobile Data Breaches
The T-Mobile data breaches involved multiple incidents, impacting millions of customers and exposing a wide range of sensitive personal data. The scale of these breaches underscores the devastating consequences of inadequate data security. While specific dates for all breaches may not be publicly available, several significant incidents have been reported.
- Specific dates of the breaches: While precise dates for all breaches aren't always publicly released due to ongoing investigations, reports indicate multiple incidents occurring over a period of time, highlighting the ongoing nature of the security challenges faced by T-Mobile.
- Types of data compromised: The compromised data included a concerning array of sensitive information. This ranged from names and addresses to Social Security numbers, driver's license information, and in some cases, financial account details. The potential for identity theft and financial fraud is significant following such a data breach.
- Number of affected customers: The total number of customers affected across multiple breaches runs into the millions, demonstrating the wide-reaching impact of the security failures. This massive scale underscores the severity of the situation and the urgent need for improved data security measures.
- Specific vulnerabilities exploited: While the exact vulnerabilities exploited in each incident aren't always publicly disclosed for security reasons, reports suggest weaknesses in network security and potentially insufficient protection against known attack vectors were factors. This highlights the importance of proactive patching and security updates.
The $16 Million Fine and Regulatory Response
The significant financial penalty levied against T-Mobile reflects the seriousness of the data breaches and the regulatory response to the company's security failures. The $16 million fine highlights the substantial costs associated with neglecting data security.
- Specific regulatory bodies involved: The Federal Trade Commission (FTC) played a key role in investigating the breaches and imposing penalties. Other agencies, including state attorneys general, may also have been involved depending on the specifics of the data breaches and the location of affected customers. Such multi-agency involvement underscores the severity of the breach.
- Specific violations cited by regulators: The violations likely include non-compliance with various data security regulations designed to protect consumer data. These might involve failing to adequately safeguard sensitive information, implement sufficient security measures, and promptly notify affected individuals of the breach.
- Breakdown of the $16 million fine: The fine encompasses penalties intended to punish the company for its negligence, as well as potential restitution to affected customers for the costs associated with identity theft and fraud prevention.
- Other consequences faced by T-Mobile: Beyond the financial penalty, T-Mobile has suffered reputational damage, impacting customer trust and potentially leading to a loss of business. This highlights the broader implications of data breaches extending beyond direct financial costs.
Analysis of Security Gaps in T-Mobile's Infrastructure
The T-Mobile data breaches exposed several significant weaknesses in the company's security infrastructure. Addressing these vulnerabilities is crucial not only for T-Mobile but also for all organizations handling sensitive data.
- Lack of multi-factor authentication: The absence or insufficient implementation of multi-factor authentication (MFA) likely contributed to the breaches, making it easier for attackers to gain unauthorized access to systems. MFA is a crucial layer of security and is recommended for all sensitive accounts.
- Inadequate data encryption: Insufficient or improperly implemented data encryption allowed attackers to access sensitive data even if they gained unauthorized access to systems. Strong encryption is paramount for protecting data at rest and in transit.
- Insufficient employee training on cybersecurity best practices: A lack of comprehensive cybersecurity awareness training for employees could have enabled attackers to exploit human vulnerabilities through phishing scams or other social engineering techniques. Ongoing training is vital for maintaining strong security.
- Weaknesses in network security: Vulnerabilities in T-Mobile's network infrastructure, such as outdated software or improperly configured firewalls, likely provided entry points for attackers. Regular security assessments and updates are essential.
- Lack of proactive security monitoring and threat detection: The absence of robust security monitoring and threat detection systems allowed attacks to go undetected for potentially extended periods, exacerbating the damage. Real-time monitoring is key to quickly identifying and responding to threats.
Lessons Learned and Best Practices for Data Security
The T-Mobile data breaches provide valuable lessons for all organizations. Implementing strong data security practices is not simply a matter of compliance; it is a fundamental business imperative.
- Implementing strong multi-factor authentication: MFA adds a critical layer of security, making it significantly harder for attackers to gain unauthorized access even if they have compromised passwords.
- Utilizing robust data encryption techniques: Encrypting sensitive data both at rest and in transit is vital to protecting it from unauthorized access, even if a security breach occurs.
- Regular security audits and penetration testing: Regularly assessing vulnerabilities through security audits and penetration testing is crucial for identifying and mitigating potential weaknesses in security systems.
- Employee cybersecurity awareness training: Providing ongoing training to employees on cybersecurity best practices is essential for mitigating human vulnerabilities exploited through phishing and social engineering attacks.
- Investing in advanced threat detection and response systems: Implementing advanced threat detection systems allows for quicker identification and response to security incidents, minimizing potential damage.
- Compliance with relevant data privacy regulations (e.g., GDPR, CCPA): Adhering to relevant data privacy regulations is not only a legal requirement but also demonstrates a commitment to protecting customer data.
Conclusion
The T-Mobile data breaches and the subsequent $16 million fine serve as a cautionary tale for all organizations handling sensitive customer data. The incident highlights the critical need for proactive and comprehensive cybersecurity measures. Failure to prioritize data security can lead to significant financial penalties, reputational damage, and erosion of customer trust. Businesses must prioritize robust data security practices to avoid the costly consequences of a T-Mobile-scale data breach. Implement strong security measures, conduct regular security assessments, and stay informed about evolving cybersecurity threats. Don't wait for a costly data breach to prioritize your information security; proactive measures are key to protecting your customers and your business from the devastating impact of a T-Mobile-level security failure.

Featured Posts
-
 Jeff Bezos Space Ambitions Falter A Bigger Blow Than Katy Perry S
Apr 22, 2025
Jeff Bezos Space Ambitions Falter A Bigger Blow Than Katy Perry S
Apr 22, 2025 -
 Robotic Limitations In Nike Sneaker Manufacturing A Detailed Look
Apr 22, 2025
Robotic Limitations In Nike Sneaker Manufacturing A Detailed Look
Apr 22, 2025 -
 Understanding Papal Conclaves Tradition Secrecy And The Election Of A New Pope
Apr 22, 2025
Understanding Papal Conclaves Tradition Secrecy And The Election Of A New Pope
Apr 22, 2025 -
 Covid 19 Pandemic Lab Owners Guilty Plea For Falsified Test Results
Apr 22, 2025
Covid 19 Pandemic Lab Owners Guilty Plea For Falsified Test Results
Apr 22, 2025 -
 Trumps Economic Legacy Winners And Losers
Apr 22, 2025
Trumps Economic Legacy Winners And Losers
Apr 22, 2025
