Office365 Executive Inbox Hacking: Millions In Losses Reported To FBI
Table of Contents
Understanding the Office365 Executive Inbox Hacking Threat
Office365 executive inbox hacking leverages various sophisticated techniques to gain unauthorized access to sensitive company data and finances. Attackers exploit vulnerabilities in individuals and systems to achieve their malicious goals. These methods include:
- Phishing and Spear Phishing: These highly targeted attacks use deceptive emails designed to trick recipients into revealing login credentials or downloading malware. Spear phishing attacks are particularly effective, as they are personalized to appear legitimate and trustworthy, often mimicking communication from known contacts or business partners. Common techniques include urgent requests for wire transfers, fake invoice payments, and urgent security alerts.
- Malware: Malicious software, often delivered through phishing emails or infected attachments, can secretly access and steal data from compromised accounts. This malware can range from keyloggers capturing keystrokes to sophisticated trojans providing complete remote control over the infected system.
- Credential Stuffing: Attackers use lists of stolen usernames and passwords obtained from previous data breaches to attempt to access Office365 accounts. This brute-force approach can be surprisingly effective if weak or reused passwords are employed.
The vulnerabilities exploited are often surprisingly basic:
- Weak Passwords: Using simple, easily guessable passwords is a major security risk.
- Lack of Multi-Factor Authentication (MFA): MFA adds an extra layer of security, requiring more than just a password to access an account. Its absence significantly increases vulnerability.
- Outdated Software: Failing to update software and applications creates exploitable vulnerabilities for attackers.
Executives are prime targets because:
- They possess access to sensitive financial information.
- They have the authority to authorize significant financial transactions.
- They are often perceived as less tech-savvy and therefore more susceptible to social engineering tactics.
The Financial Ramifications of Compromised Office365 Accounts
The financial consequences of successful Office365 executive inbox hacking can be catastrophic. The FBI has documented numerous cases resulting in millions of dollars in losses. These losses stem from various types of fraud:
- Wire Transfer Fraud: Hackers manipulate email communications to redirect payments intended for legitimate vendors to their own accounts.
- Invoice Fraud: Fraudulent invoices are sent, disguised as legitimate business expenses, leading to unauthorized payments.
- Ransomware Attacks: Data is encrypted, and the business is forced to pay a ransom for its release.
The impact extends beyond immediate financial losses:
- Example: A recent case saw a company lose $2 million due to a successful wire transfer fraud orchestrated via a compromised executive email account. (Source: Insert credible news source or report here)
- Reputational Damage: A data breach can severely damage a company's reputation, impacting customer trust and investor confidence.
- Legal Ramifications: Businesses face potential lawsuits from customers, partners, and regulatory bodies.
- Regulatory Fines: Non-compliance with data protection regulations can result in substantial fines.
Best Practices for Preventing Office365 Executive Inbox Hacking
Implementing robust security measures is paramount to preventing Office365 executive inbox hacking. This requires a multi-layered approach:
- Strong Password Policies: Enforce complex, unique passwords and encourage the use of password managers.
- Multi-Factor Authentication (MFA): Mandate MFA for all Office365 accounts, especially executive accounts. This adds a significant layer of security by requiring a second form of verification, such as a code from a mobile app or a security key.
- Regular Security Awareness Training: Educate employees, particularly executives, about phishing techniques, social engineering tactics, and the importance of cybersecurity best practices. Regular training should simulate real-world scenarios and reinforce appropriate responses.
- Email Security Solutions: Utilize advanced email filtering and anti-phishing tools to detect and block malicious emails before they reach inboxes.
- Regular Software Updates and Patching: Ensure all software and applications are up-to-date with the latest security patches.
- Regular Security Audits and Penetration Testing: Conduct regular security assessments to identify and address vulnerabilities.
- Advanced Threat Protection (ATP): Leverage Office 365's built-in ATP features to detect and prevent advanced threats.
Reporting and Responding to Office365 Executive Inbox Hacking Incidents
If an executive's inbox is compromised, immediate action is crucial:
- Isolate Affected Accounts: Immediately change passwords and disable access to the compromised account.
- Report the Incident: Contact the FBI’s Internet Crime Complaint Center (IC3) and other relevant authorities.
- Conduct a Thorough Investigation: Determine the extent of the breach and the data compromised.
- Data Recovery and Remediation: Implement procedures to recover data and restore systems.
- Post-Incident Analysis: Conduct a thorough review to identify vulnerabilities and implement preventative measures.
Developing and regularly testing an incident response plan is crucial to minimizing the impact of a breach.
Conclusion: Safeguarding Your Business from Office365 Executive Inbox Hacking
Office365 executive inbox hacking presents a significant threat, exposing businesses to substantial financial losses and reputational damage. Implementing robust security measures, including strong password policies, MFA, regular security awareness training, and advanced email security solutions, is critical. Proactive security measures are the best defense against these attacks. Don't wait until it's too late – take decisive action to protect your organization from the devastating consequences of Office365 executive inbox hacking. For further resources on enhancing your email security and threat protection, consult reputable cybersecurity organizations and industry best practice guides.

Featured Posts
-
 7
Apr 24, 2025
7
Apr 24, 2025 -
 John Travoltas Emotional Birthday Post For His Late Son Jett
Apr 24, 2025
John Travoltas Emotional Birthday Post For His Late Son Jett
Apr 24, 2025 -
 Zaboravljeni Projekt Film S Travoltom Koji Tarantino Ne Zeli Vidjeti
Apr 24, 2025
Zaboravljeni Projekt Film S Travoltom Koji Tarantino Ne Zeli Vidjeti
Apr 24, 2025 -
 Optimus Robot Development How Chinas Rare Earth Policy Creates Challenges For Tesla
Apr 24, 2025
Optimus Robot Development How Chinas Rare Earth Policy Creates Challenges For Tesla
Apr 24, 2025 -
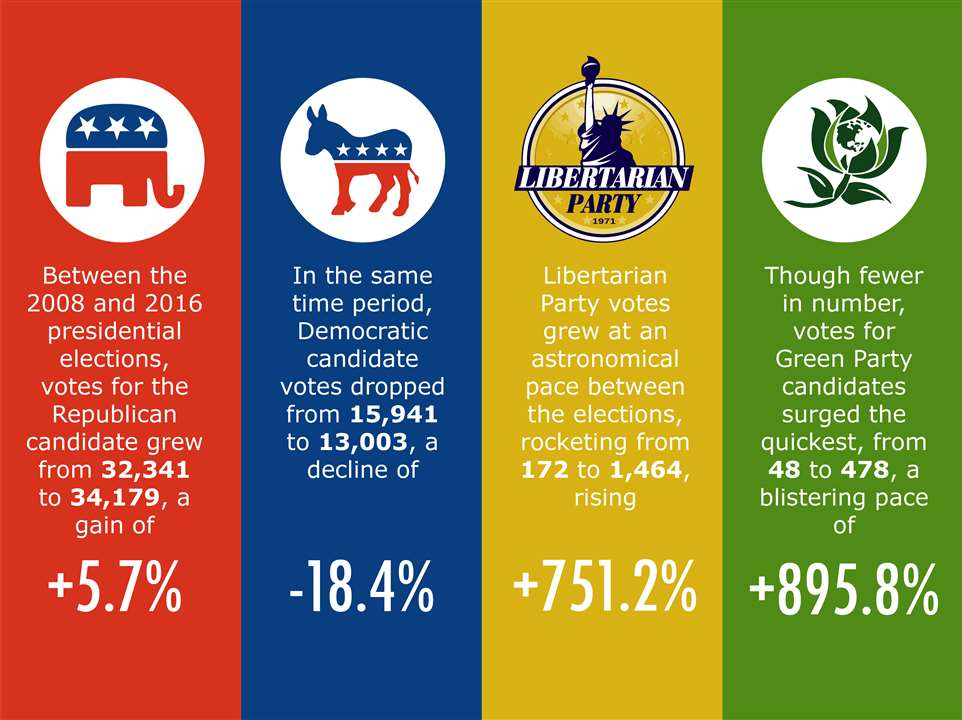 William Watson Examining The Liberal Party Platform Before You Vote
Apr 24, 2025
William Watson Examining The Liberal Party Platform Before You Vote
Apr 24, 2025
