Office365 Breach Nets Millions For Hacker, FBI Says
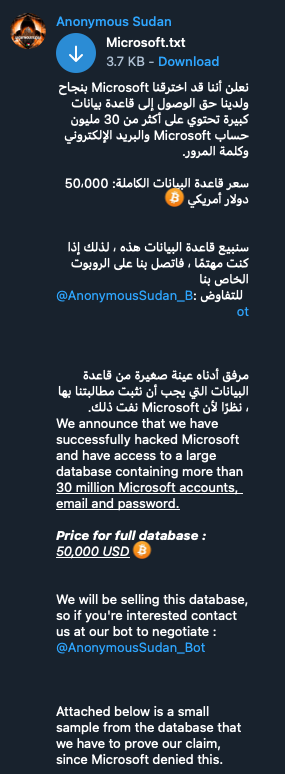
Table of Contents
Details of the Office365 Breach
The Method of Attack
The FBI investigation suggests the hackers exploited several vulnerabilities to gain access to the targeted Office365 accounts. The attack likely involved a combination of sophisticated techniques:
- Phishing campaigns: Highly targeted phishing emails were sent, mimicking legitimate communications from trusted sources. These emails contained malicious links or attachments designed to deliver malware.
- Credential stuffing: Stolen usernames and passwords from previous data breaches were used to attempt logins to Office365 accounts. Weak or reused passwords made this attack vector particularly effective.
- Exploitation of unpatched software: The hackers may have leveraged known vulnerabilities in outdated Office365 applications or related software to gain unauthorized access. This highlights the critical importance of regular software updates.
Specific Office365 applications targeted included Exchange Online (for email compromise), SharePoint (for accessing sensitive documents), and OneDrive (for stealing files stored in the cloud).
The Scale of the Breach
The full extent of the Office365 breach is still emerging, but initial reports indicate a significant impact:
- Hundreds of users affected: The number of compromised accounts is likely in the hundreds, potentially impacting numerous organizations.
- Millions of dollars stolen: The financial losses suffered by victims are estimated to be in the millions, encompassing both direct monetary theft and the costs of remediation.
- Sensitive data compromised: The stolen data included a range of sensitive information, including financial records, customer data, intellectual property, and confidential business communications. Industries targeted included finance, healthcare, and technology.
The FBI's Involvement
The FBI is actively investigating the Office365 breach, working to identify the perpetrators and recover stolen assets. Their efforts include:
- Tracing the digital footprint: The FBI is tracking the hackers' online activities to identify their location and other details.
- Collaboration with international agencies: This is likely a transnational crime, requiring cooperation with law enforcement agencies in other countries.
- Public awareness campaign: The FBI is likely to issue public service announcements to educate organizations and individuals about cybersecurity best practices to prevent future Office365 breaches.
The Financial and Reputational Impact
Financial Losses
The financial repercussions of the Office365 breach extend beyond the direct theft of funds:
- Direct monetary losses: Millions of dollars were stolen directly from affected accounts.
- Remediation costs: Organizations face significant costs associated with investigating the breach, recovering data, and implementing improved security measures.
- Legal liabilities: Affected organizations may face legal action from customers and regulatory bodies, leading to further financial penalties. Data breach fines can be substantial.
Reputational Damage
Beyond financial losses, the Office365 breach causes significant reputational harm:
- Loss of customer trust: The breach erodes customer confidence, potentially leading to a loss of business.
- Damage to brand image: A data breach can severely damage an organization's reputation, making it difficult to attract new customers and partners.
- Impact on investor confidence: The breach may negatively affect stock prices and investor confidence in the affected organization.
Preventing Future Office365 Breaches
Strengthening Passwords and Authentication
Strong passwords and multi-factor authentication (MFA) are crucial for preventing unauthorized access:
- Use strong, unique passwords: Choose passwords that are long, complex, and unique to each account.
- Implement multi-factor authentication: MFA adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone or a security key.
- Use a password manager: A password manager can help you generate and securely store strong, unique passwords for all your accounts.
Regular Software Updates and Patching
Promptly updating software is essential to address known vulnerabilities:
- Automatic updates: Enable automatic updates for Office365 and other relevant software to ensure that security patches are applied promptly.
- Regular patching schedule: Establish a regular schedule for checking for and installing updates.
- Test updates in a sandbox environment: Before deploying updates to your entire system, test them in a controlled environment.
Employee Training and Security Awareness
Educating employees about cybersecurity threats is critical:
- Regular security awareness training: Provide employees with regular training on phishing scams, social engineering attacks, and other cybersecurity threats.
- Security awareness campaigns: Conduct regular campaigns to reinforce security best practices and raise awareness among employees.
- Simulated phishing attacks: Conduct simulated phishing attacks to test employee awareness and identify vulnerabilities.
Data Encryption and Backup Strategies
Protecting data through encryption and robust backups is crucial:
- Encrypt data both in transit and at rest: Use encryption to protect data while it's being transmitted and when it's stored.
- Implement a robust backup and recovery plan: Regularly back up your data to a secure location and have a plan in place for recovering data in the event of a breach.
- Use cloud-based backup solutions: Consider using a cloud-based backup solution to ensure data redundancy and disaster recovery capabilities.
Conclusion
The recent Office365 breach, resulting in millions of dollars stolen, serves as a stark warning about the vulnerability of even the most sophisticated cloud-based systems. The financial and reputational consequences of such breaches can be devastating. To prevent future Office365 data breaches, organizations must prioritize strong passwords and authentication, regular software updates, comprehensive employee training, and robust data encryption and backup strategies. Ignoring these crucial steps leaves your organization exposed to significant risks. Review your Office365 security protocols today, implement best practices, and consider consulting cybersecurity experts to fortify your defenses against Office365 data breaches and other cyber threats. Learn more about securing your Office365 environment and protecting your valuable data.

Featured Posts
-
 Abu Dhabi 2024 1 1bn Investments 26 2bn Real Estate Boom And More
Apr 28, 2025
Abu Dhabi 2024 1 1bn Investments 26 2bn Real Estate Boom And More
Apr 28, 2025 -
 Twins Win 6 3 Over Mets Taking Game Two Of Series
Apr 28, 2025
Twins Win 6 3 Over Mets Taking Game Two Of Series
Apr 28, 2025 -
 Unexpected Trump Zelensky Encounter Precedes Popes Funeral
Apr 28, 2025
Unexpected Trump Zelensky Encounter Precedes Popes Funeral
Apr 28, 2025 -
 Is Kuxius Solid State Power Bank Worth The Higher Price
Apr 28, 2025
Is Kuxius Solid State Power Bank Worth The Higher Price
Apr 28, 2025 -
 Funeral Of Pope Francis A Gathering Of World Leaders
Apr 28, 2025
Funeral Of Pope Francis A Gathering Of World Leaders
Apr 28, 2025
