Hegseth's Private Signal Messages: Details Of Military Strategies Disclosed

Table of Contents
Content of the Leaked Messages
The leaked messages, allegedly communicated via [Specify communication platform, e.g., a secure messaging app or email], reveal a concerning level of detail regarding ongoing military operations. The tone of the messages suggests a degree of informality, which raises questions about the appropriate handling of sensitive information.
- Specific examples of military strategies or information potentially disclosed: While the exact content remains classified, reports suggest discussions about troop deployments in [Location 1], the planned use of [Type of weapon/technology] in [Location 2], and potential responses to [Specific geopolitical event]. The level of detail disclosed raises serious questions about operational security.
- Types of operations or locations discussed: Sources suggest the messages covered a range of operations, including counter-terrorism efforts, strategic deployments, and intelligence gathering, with specific locations mentioned including [Location 3] and [Location 4]. The breadth of information contained in Hegseth's private signal messages is alarming.
- Assessment of the credibility of the leaked information: While the authenticity of the leaked messages is still under investigation, multiple sources corroborate the presence of information consistent with classified military strategy. Independent verification efforts are underway to confirm the credibility of the disclosed data.
Potential Sources of the Leak
Determining the source of this leak is paramount. Several avenues are being explored:
- Analysis of vulnerabilities in communication systems used: Investigators are scrutinizing the security protocols of the communication platform used by [Hegseth's Name/Title], looking for potential weaknesses exploited by malicious actors. This includes examining potential software vulnerabilities, insufficient encryption, or human error in security practices.
- Discussion of potential motives for the leak: Potential motives range from intentional espionage, seeking to benefit a foreign power, to accidental disclosure due to negligence or a compromised device. The possibility of whistleblowing, driven by ethical concerns or a desire for transparency, is also being investigated.
- Mention any ongoing investigations into the source of the leak: Multiple agencies, including [Mention relevant agencies, e.g., the Department of Defense, FBI, or NSA], are actively pursuing the investigation, leaving no stone unturned to identify the source of the Hegseth's private signal messages leak.
Implications and Consequences
The implications of this leak are far-reaching and potentially catastrophic:
- Impact on ongoing military operations: The disclosure of sensitive information could severely compromise ongoing military operations, potentially jeopardizing the safety of personnel and the success of missions. Operational security breaches of this magnitude can have devastating effects.
- Risk to personnel involved in the disclosed strategies: Individuals whose identities or locations were revealed in the leaked messages are now at heightened risk, requiring immediate protective measures. The safety and well-being of those involved are the top priority.
- Potential damage to international relations: The leak could damage trust and cooperation between nations, potentially exacerbating existing geopolitical tensions and hindering diplomatic efforts. This damage could extend far beyond the immediate security implications.
- Legal ramifications for those involved: Those found responsible for the leak, whether through negligence or malicious intent, face severe legal repercussions, including lengthy prison sentences and significant fines. The legal consequences are severe and far-reaching.
The Ongoing Investigation and Response
The official response has been swift, focused on containment and investigation:
- Statements made by relevant authorities: [Mention statements made by relevant officials, e.g., “The Department of Defense is taking this matter extremely seriously…”].
- Actions taken to address vulnerabilities in communication systems: Immediate steps have been taken to enhance security protocols and address any identified vulnerabilities within the communication systems used by military personnel, including upgrading encryption protocols and improving employee training.
- Update on the status of the investigation: The investigation is ongoing, with authorities committed to identifying those responsible and preventing future leaks. This investigation is a top priority for national security.
Conclusion
The leak of Hegseth's private signal messages represents a significant breach of national security, potentially compromising military strategies and endangering personnel. The ongoing investigation aims to identify the source of the leak and address the vulnerabilities that allowed it to occur. The potential consequences – ranging from disrupted military operations to damaged international relations – are severe. The situation highlights the crucial need for robust cybersecurity measures and the importance of safeguarding sensitive information. Stay informed about this developing story and the ongoing investigation into Hegseth's private signal messages. Monitor credible news sources for updates on the situation and its ramifications. Understanding the details surrounding this leak is crucial for assessing the ongoing threats to national security. Continue researching Hegseth's private signal messages to stay up to date on this important issue.

Featured Posts
-
 Federal Trade Commission Launches Probe Into Open Ai And Chat Gpt
Apr 22, 2025
Federal Trade Commission Launches Probe Into Open Ai And Chat Gpt
Apr 22, 2025 -
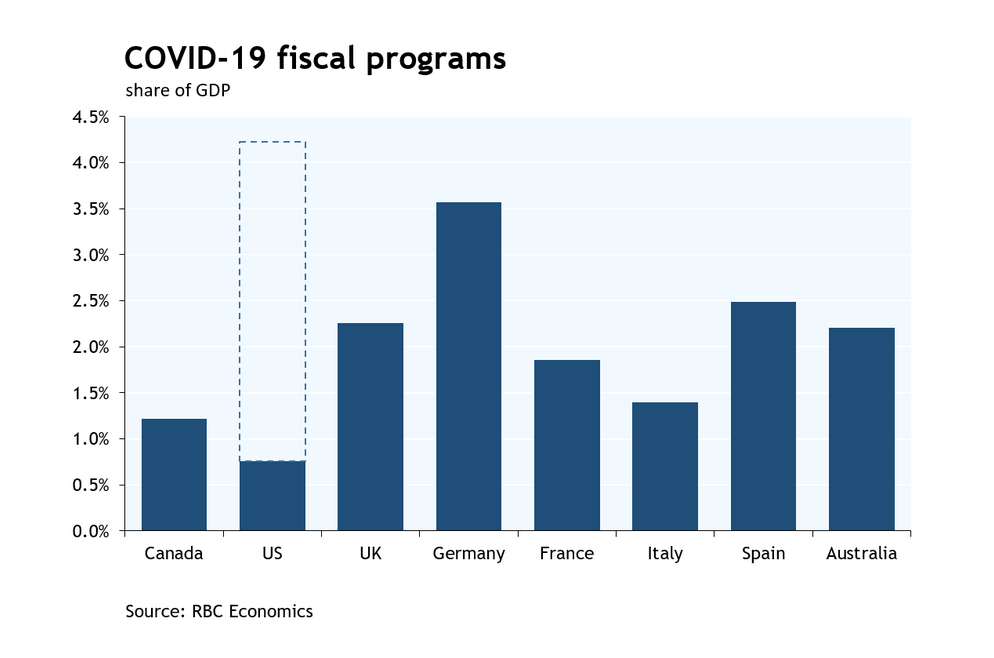 Bank Of Canada Holds Rates What Economists Say In Fp Video Interview
Apr 22, 2025
Bank Of Canada Holds Rates What Economists Say In Fp Video Interview
Apr 22, 2025 -
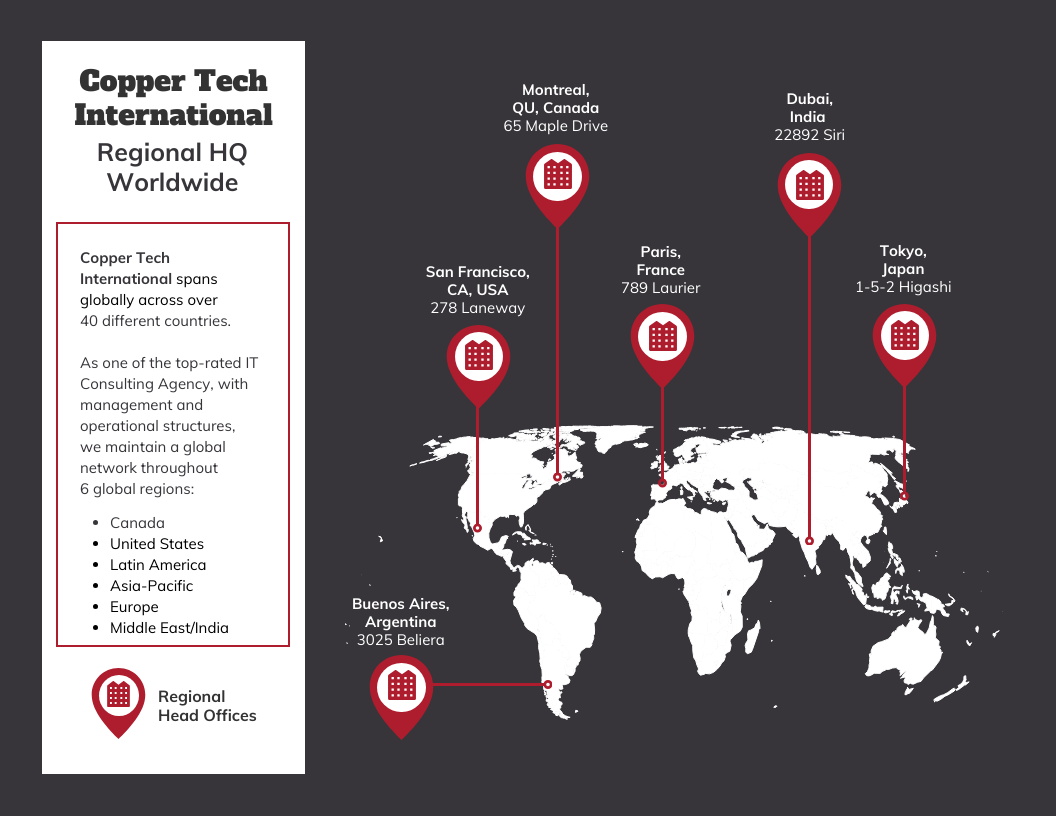 Where To Start A Business A Map Of The Countrys Best Locations
Apr 22, 2025
Where To Start A Business A Map Of The Countrys Best Locations
Apr 22, 2025 -
 A Comprehensive Guide To The Countrys Emerging Business Hotspots
Apr 22, 2025
A Comprehensive Guide To The Countrys Emerging Business Hotspots
Apr 22, 2025 -
 Hegseth Faces Backlash Over Leaked Signal Chat And Pentagon Claims
Apr 22, 2025
Hegseth Faces Backlash Over Leaked Signal Chat And Pentagon Claims
Apr 22, 2025
